Cybersecurity Certifications | Your guide to securing your IT infrastructure in 2024
Cybersecurity Certifications | Your guide to securing your IT infrastructure in 2024
Why the need for cybersecurity certifications?
We spend so much time on the internet using our mobile devices. We also tend to input quite a lot of sensitive data when we shop, do our online banking, and communicate with people from all around the globe.
The lines between our digital and physical world have been increasingly blurred into one – especially in this new normal. But this has only increased our exposure and risk to cyberthreats. One wrong click or tap could potentially lead to your privacy and safety being jeopardized.
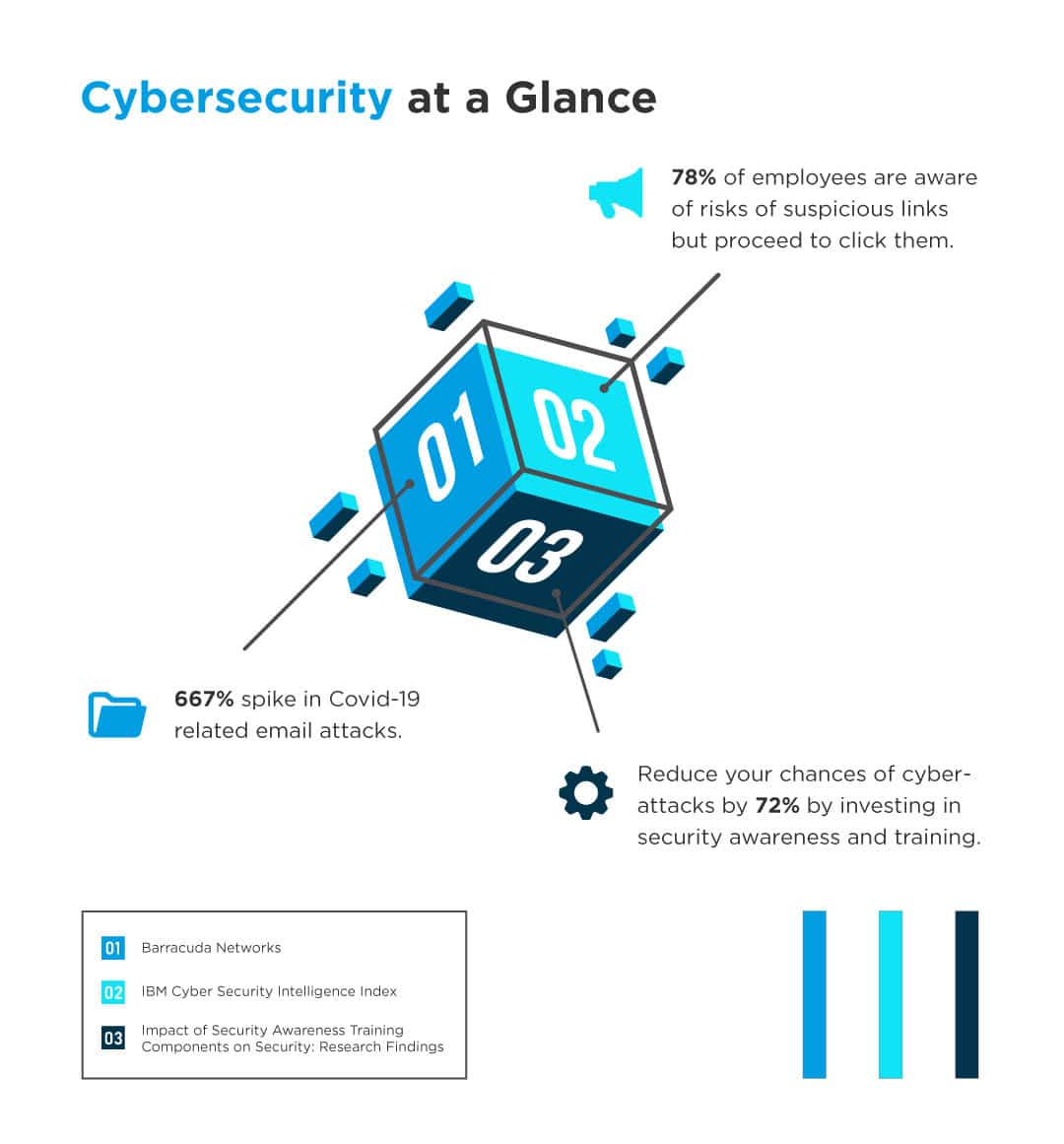
According to the Nexusguard’s Annual Threat Report 2020, cyber attackers aimed their target on the backs of industries providing connectivity, services and entertainment to people that have been forced into a lockdown and a work-from-home situation.
With social distancing measures implemented across the globe, 2020 also caused a boom in online gaming as well as a high reliance on the internet which made it a very inviting target for attackers. The motivation for these cyberattacks are oftentimes aplenty and varied – sometimes, for economic and political gains and other times for fiscal benefits.
The report also revealed that distributed denial-of-service (DDoS) attacks during the pandemic has resulted in 341% year-over-year increase. Whilst Nexusguard has also predicted that ransom DDoS (RDDoS) attacks will increase 30% coming year.
.
Similarly, IBM Cyber Security Intelligence Index disclosed that 95% of data breaches were caused by human error. With hacking methods becoming more discerning with every passing year, there is a continuous reinforcement on how important cybersecurity training is to keep your organization safe.
The Importance of Cybersecurity Training for Your Organization
Your team is an integral element in safeguarding your organization from cyberattacks. Within your daily operations, your team members will quite likely be handling sensitive data while dealing with clients – a small slip in managing sensitive data could lead to major regulatory issues as well as reputational damages. Phishing scams are also another common way that that your security could be compromised and depending on the type of breach could cause operational disruptions. Likewise, poor password practices also have a notoriety for negatively impacting your defenses against attacks.
These instances are just a few of many reasons why cybersecurity training is imperative for every organization. Educating your team is the first and foremost effective way in combatting and strengthening your first line of defense. It is important for them to learn about risk mitigation, as well as the steps to take should something wrong happen. It is known that even the with the most state-of-the-art security system and toughened firewalls, you can’t keep hackers out when you, yourself, have opened the doors to let them in.
Cybersecurity as a Career
In a Forbes article it was revealed that one of the biggest pain points that most chief information security officers (CISO) have now is – the lack of people with security skill on the team.
In a survey conducted involving 200 CISO’s found that the issue lies in talent and training constraints. Additionally, organizations with a siloed approach to security negatively impacts an organization versus those that approach it with an enterprise-wide strategy.
Along with the increase of cyber attacks and booming rise of cyberthreats, there is an urgent demand for skilled professionals within the cybersecurity field. Fill in the skill gap and reap the benefits of an accelerated career growth within the cybersecurity field.

.
Cybersecurity Fundamentals
Build a solid foundation and gain essential insights required to navigate the world of cybersecurity. Through these fundamentals courses you will discover the basic concepts of security, compliance management, risk analysis, conducting security assessments to detect vulnerabilities, insights on the future of security, exploring various perspective of security and much more.
| Code | Course Title | Days | Fees (RM) | Jan-24 | Feb-24 | Mar-24 |
|---|---|---|---|---|---|---|
| AWS-SE | AWS Security Essentials | 1 | 1,800 | – | – | 5 |
| SC-900 | Microsoft Security, Compliance and Identity Fundamentals | 1 | 1,200 | – | 26 | – |
| CT-Security+ | CT-SECURITY+: CompTIA Security+ | 5 | 3,500 | 29-2 | – | 18-22 |
| CSAU | Certified Security Aware User | 1 | 1,000 | – | – | – |
Cybersecurity Engineer
As a cybersecurity engineer your role requires you to safeguard your organization and strengthen your first line of defense. The fast-paced role is an essential part of any organizational that requires you to keep up with new hacking trends and new cyberthreats. Explore these courses to gain insights from industry experts who understands the essential and requirements of Cybersecurity. Explore these roles to be empowered in securing your organization against serious cyber threats.
| Code | Course Title | Days | Fees (RM) | Jan-24 | Feb-24 | Mar-24 |
|---|---|---|---|---|---|---|
| AWS-SEC | Security Engineering on AWS | 3 | 5,400 | – | – | 6-8 |
| CCSP | Certified Cloud Security Professional | 5 | 8,500 | 29-2 | – | 18-22 |
| SSCP | Systems Security Certified Practitioner | 5 | 7,500 | 8-11 | – | 5-8 |
| RCCE1 | Rocheston Certified Cybersecurity Engineer – Level 1 | 5 | 6,500 | 29-2 | – | 18-22 |
| RCCE2 | Rocheston Certified Cybersecurity Engineer – Level 2 | 5 | 6,500 | – | 19-23 | – |
| RH415 | Red Hat Security: Linux in Physical, Virtual and Cloud | 5 | 9,000 | – | – | – |
| SC-300 | Microsoft Identity and Access Administrator | 4 | 3,000 | – | – | 5-8 |
| GCSEC | Security in Google Cloud Platform | 2 | 4,800 | – | – | 6-8 |
| CSX-P | Certified Cybersecurity Practitioner | 5 | 9,500 | – | – | – |
Penetration Tester
The role of a penetration tester is responsible in performing cyberattack simulations on an organization’s computer system and network, playing the key role of a ‘bad guy’ in finding holes within the network. These holes must be plugged to ensure there are no vulnerabilities to the security system. Tests are conducted by utilizing a variety of hacking tools and techniques to find these holes. Documenting each detail and creating a report on the success of breaching security protocols.
| Code | Course Title | Days | Fees (RM) | Jan-24 | Feb-24 | Mar-24 |
|---|---|---|---|---|---|---|
| CT-Pentest | CT-PENTEST+: CompTIA PenTest+ | 5 | 3,500 | – | 19-23 | – |
| CPT | Certified Penetration Tester | 5 | 5,500 | – | – | – |
Security Operations Center
A security operations center (SOC) analyst is responsible to monitor and fight cyberthreats to an organization’s IT (Information Technology) infrastructure, identifying security weaknesses and opportunities as first responders during security. They are required to work well under pressure to scope out technological crimes, juggle, multiple critical tasks spanning technical, analytical, and business areas as well as implement changes to avoid re-occurrences.
| Code | Course Title | Days | Fees (RM) | Jan-24 | Feb-24 | Mar-24 |
|---|---|---|---|---|---|---|
| SC-200T00 | Microsoft Security Operations Analyst | 4 | 3,000 | – | 27-1 | – |
| CBROPS | Understanding Cisco Cybersecurity Operations Fundamentals v1.0 | 5 | 12,000 | 15-19 | – | 18-22 |
| CSOCA | Certified Security Operation Center (SOC) Analyst | 5 | 5,500 | – | – | – |
Cybersecurity Analyst
As a cybersecurity analyst you will be responsible to sniff out cyberthreats before they happen to stop these cybercriminals in their tracks. They oftentimes simulate security attacks to find out potential vulnerabilities. With the hackers continuously implementing new strategies, analysts will also need to be alert of the various developments within the security field.
| Code | Course Title | Days | Fees (RM) | Jan-24 | Feb-24 | Mar-24 |
|---|---|---|---|---|---|---|
| CT-CySA | CT-CYSA+: CompTIA Cybersecurity Analyst | 5 | 3,500 | 15-19 | – | 11-15 |
| Secur201 | Implementing an Integrated Threat Defense Solution | 2 | 8,000 | – | – | – |
| Secur202 | Implementing an Integrated Threat Defense Investigation and Mitigation | 2 | 8,000 | – | – | – |
| CSOCA | Certified Security Operation Center (SOC) Analyst | 5 | 6,300 | – | – | – |
| CCTIA | Certified Cyber Threat Intelligence Analyst | 5 | 6.300 | – | – | – |
| CISM | Certified Information Security Manager | 4 | 9,000 | – | 26-29 | – |
| SC-400 | Microsoft Information Protection Administrator | 2 | 2,100 | – | – | 5-8 |
In today’s digital world, where cyber attacks are becoming more common and sophisticated, it is crucial for organizations to hire skilled cybersecurity professionals who are certified in their field. These professionals can help protect an organization from data breaches, ransomware attacks, and other cyber threats, which can have serious consequences, such as financial losses, reputational damage, and loss of customer trust.
By hiring skilled cybersecurity professionals with the right certifications, organizations can ensure that they have the necessary expertise to defend themselves against cyber attacks and keep their sensitive data and systems secure.
Frequently Asked Questions
Are cybersecurity certifications worth my time?
In general, cybersecurity certifications can be worthwhile for individuals who want to advance their careers in the field of cybersecurity. These certifications can demonstrate to employers that an individual has the knowledge and skills necessary to perform the tasks required in a cybersecurity job. Additionally, many organizations require employees in certain cybersecurity roles to hold certain certifications, so having a certification can make an individual more competitive in the job market. Of course, the value of a certification will depend on the specific certification and the individual’s career goals, so it’s important to do some research and choose a certification that aligns with your career aspirations.
Is it worth to pursue a career in cybersecurity?
A career in cybersecurity can be very rewarding, both financially and personally. The demand for skilled cybersecurity professionals continues to grow, and as a result, individuals with expertise in this field can often command high salaries. Additionally, the work can be challenging and varied, allowing individuals to constantly learn and develop their skills.
However, it’s important to keep in mind that a career in cybersecurity can also be demanding, with long hours and the need to stay up-to-date on the latest threats and technologies. Additionally, the work can be stressful, as individuals in this field are responsible for protecting sensitive information and systems from attack.
Overall, pursuing a career in cybersecurity can be a great choice for individuals who are interested in technology, have strong problem-solving skills, and are willing to work hard and continuously learn. It can be a challenging but rewarding field that offers many opportunities for career advancement.
What are the top paying jobs in cybersecurity
The top paying jobs in cybersecurity can vary depending on factors such as location, experience, and education. However, in general, some of the highest paying jobs in the field include positions such as:
- Chief Information Security Officer (CISO)
- Security Architect
- Security Manager
- Security Consultant
- Security Engineer
These roles typically require a high level of experience and education, and they often involve leading teams of cybersecurity professionals, designing and implementing security systems, and developing and implementing security policies and procedures. Individuals in these positions can earn salaries that are higher than the average for the field. Of course, the exact salary for a given position will depend on factors such as the specific job duties and the employer.




